Security Assessment And Management As a Service
EXCLUSIVELY FOR NYSBA MEMBERS
Security Assessment
Plus
An efficient and cost-effective offering that incorporates a comprehensive evaluation rather than a single stand-alone test.
Request a Quote for Security Assessment And Management As a Service
Security Assessment
Pro
A comprehensive service for security audit and amendment requirements, recommendation, risk analysis, and penetration testing.
Request a Quote for Security Assessment And Management As a Service
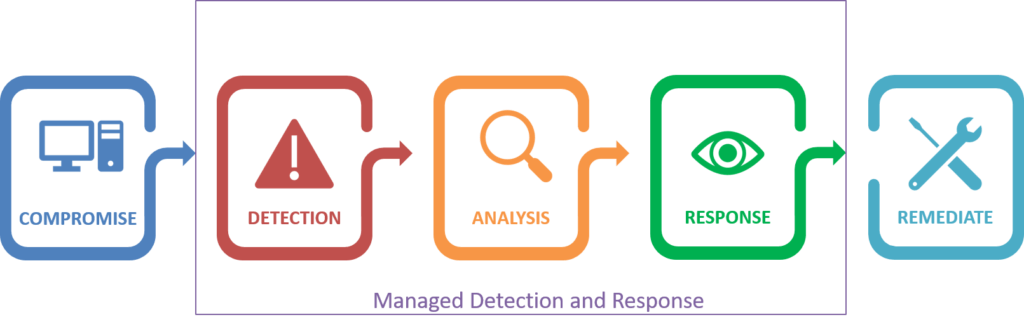
Managed Detection
and Response
Provides people, process, and technology to protect your critical infrastructure, improve your security posture and reduce risk.
Request a Quote for Security Assessment And Management As a Service
About JDL
The Evolution of Security
Basic
- Passwords / Active Directory
- Patch Management.
- Backups
Perimeter
- Firewalls
- SPAM / Web Filters
- Web Application Firewall / Proxy
Defense-In-Depth
- Anti Virus / Advance Endpoint Protection
- Data Loss Prevention / SSL
- Anti – DDoS / Intrusion Detection Systems / Cloud Access Security Broker
Detection & Response
- Log Aggregation & Correlation
- Human / Threat Intelligence
- Incident Detection and Response
Containment & Remediation
- Intrusion Containment
- Remediation
- Policy Update
Security Assessment as a Service
JDL Group provides access to all the latest security tools and systems. We specialize in outsourced assessment, management and monitoring of all IT systems and devices.
Key Features
Application Vulnerability Assessment
- Identify, quantify, and prioritize vulnerabilities in an application
- Provide threat awareness and risk background
Network Security Assessment
- Identify and assign severity levels to security defects present in system or network
Log Monitoring
- Determine what is happening on network
- Logging records the traffic passing through the network
Penetration Tests
- Attempt to exploit system vulnerabilities
- Includes OS, Service and application flaws, improper configurations
- Risky end-user behavior
Dark Web Scan
- Discover compromised passwords from your Domain.
- Prospects data and credentials exposed via the dangerously untraceable dark web.
Security Policy Review
- Assist development and review of security policies
- Support to improve Security practices
Managed Detection and Response
We will assess your organization and provide the right security services for you. Data loss prevention, risk assessment, and network infrastructure are just a few of the services we offer.